Local area networks (LAN) are an important part of modern network architecture, but as the number of devices increases, traditional broadcast networks face performance bottlenecks and security risks. Virtual LAN (VLAN) came into being, which logically divides the physical LAN into multiple independent broadcast domains, effectively solving the shortcomings of traditional LANs. This article will delve into the working principles, advantages, application scenarios and FAQs of VLAN to help you fully master this key network technology.
What Is VLAN
Virtual LAN (VLAN) is a technology that creates multiple broadcast domains by logically dividing them on a local area network (LAN). It divides a physical LAN into multiple logical LANs so that devices in each logical LAN can communicate with each other but cannot directly broadcast to other logical LANs.
1. Differences from traditional LAN
Traditional LANs use physical isolation to divide broadcast domains, such as using different network cables to connect devices to different switches. This method is more cumbersome and less flexible.
VLAN implements the division of broadcast domains through logical division, that is, allocating different ports or devices to different VLANs through software configuration. This approach is more flexible and easier to manage.
for example:
Suppose there are 100 computers in a company, 50 of which are used for office work and 50 for production. To improve network performance and security, companies want to separate office and production networks.
The traditional LAN approach is to use two switches, with office computers connected to one switch and production computers connected to the other switch.
With VLAN, only one switch is needed. Just configure the office computer’s port to one VLAN and the production computer’s port to another VLAN.
2. VLAN core idea
Core idea: The core idea of VLAN is to reduce the size of the broadcast domain through logical division, thereby improving network performance and security.
Broadcast domain: In a LAN, all broadcast traffic is received by all devices connected to the same broadcast domain. As the network scale continues to expand, broadcast traffic will increase dramatically, leading to network congestion and security risks.
Logical division: VLAN divides the LAN into multiple logical broadcast domains. Devices in each logical broadcast domain can only receive broadcast traffic from this domain, but cannot receive broadcast traffic from other broadcast domains.
for example:
Let’s say there are 20 computers in an office connected to the same switch. If one of the computers sends a broadcast, all 20 computers receive it.
Using VLAN, these 20 computers can be divided into two VLANs, one for office and one for entertainment. In this way, broadcasts sent by office computers will only affect other office computers and not entertainment computers.
3. VLAN key technologies
Port division: The most commonly used VLAN division method is based on port division. Assign different ports to different VLANs by configuring the port properties of the switch.
Protocol encapsulation: In order for devices between different VLANs to communicate with each other, VLAN tags need to be encapsulated in data packets. VLAN tags are usually encapsulated in the header of Ethernet frames.
Port division example:
Let’s say there are 10 ports on a switch, 5 for office and 5 for production. We can configure ports 1-5 as VLAN 10 (office VLAN) and ports 6-10 as VLAN 20 (production VLAN).
Protocol encapsulation example:
When one office computer sends data to another office computer, the packet is encapsulated with a VLAN 10 tag. After the switch receives the packet, it forwards the packet to the corresponding output port based on the VLAN tag, which is the port of another office computer.
How VLAN works
1. Data packet forwarding process
1.1 The data packet reaches the switch: When the data packet reaches the switch, the switch first checks the frame header of the data packet to look for the VLAN tag contained in it.
1.2 Identify VLAN: If the packet contains a VLAN tag, the switch will identify the packet as belonging to a specific VLAN based on the VLAN tag.
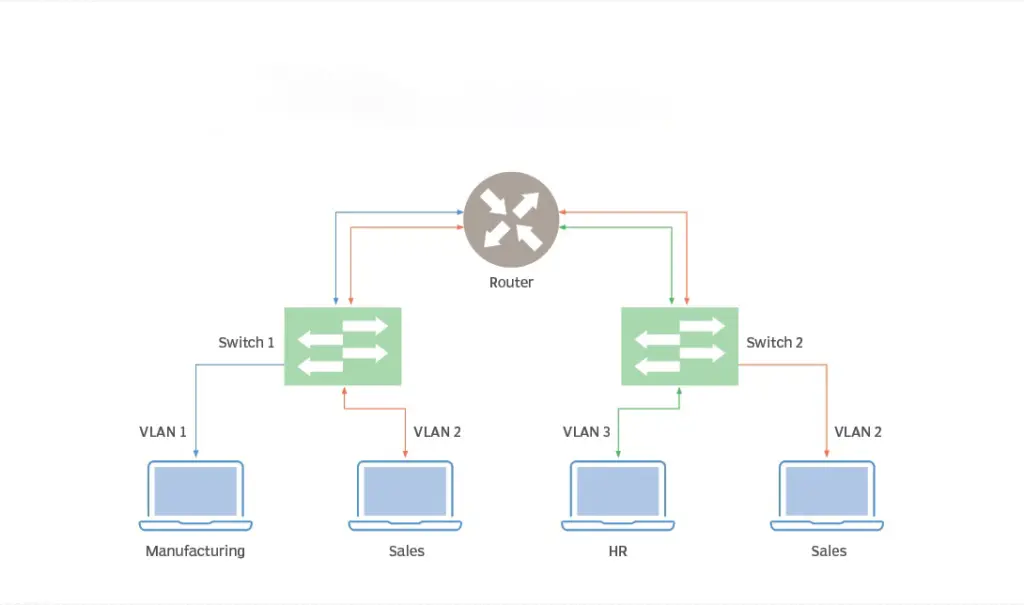
1.3 Forward the packet: The switch will look for the destination of the packet.
- If the destination is within the same VLAN: the switch forwards the packet directly to the destination port.
- If the destination is not in the same VLAN: the switch sends the packet to a router or layer 3 switch connected to the destination VLAN.
1.4 Special circumstances
- If there is no VLAN tag in the packet: the switch will forward the packet to the corresponding VLAN based on the port’s PVID (default VLAN ID).
- If the destination MAC address is unknown: the switch floods the packet to all ports within the VLAN that belongs to that port.
Example:
Suppose there are two ports on a switch, port 1 belongs to VLAN 10 and port 2 belongs to VLAN 20. When a device in VLAN 10 sends data to another device in VLAN 20, the packet is forwarded as follows:
- The packet arrives at the switch.
- The switch recognizes that the packet belongs to VLAN 10.
- The switch looks for the port corresponding to the target MAC address.
- Since the destination MAC address is unknown, the switch floods the packet to port 2.
- Port 2 receives the packet and forwards it to the destination device in VLAN 20.
2. Relationship between VLAN and MAC address and IP address attributes
2.1 MAC address: VLAN has no direct relationship with MAC address. MAC addresses are used to physically identify network devices, while VLANs are used to logically divide broadcast domains.
2.2 IP address: VLAN has no direct relationship with IP address. IP addresses are used to identify logical addresses of network devices, while VLANs are used to divide broadcast domains.
2.3 Special cases: In some cases, VLANs can be dynamically assigned by MAC address or IP address.
- VLAN based on MAC address: The switch can dynamically assign devices to different VLANs based on MAC address.
- Protocol-based VLAN: The switch can dynamically assign devices to different VLANs based on IP addresses or other protocol information.
Powerful advantages of VLAN
As an important network technology, VLAN has many advantages, making it widely used in enterprise networks, data centers, campus networks and other scenarios. Below we’ll dive into three major advantages of VLANs:
1. Improve network performance
Reduce broadcast traffic:
- Broadcasts in traditional LANs are sent to all devices connected to the same network, even if most devices do not need to receive the broadcast. This can cause network congestion and reduce network performance.
- VLAN divides the LAN into multiple logical broadcast domains, allowing broadcasts to be propagated only within specific VLANs, thus effectively reducing broadcast traffic and reducing network burden.
Reduce network congestion:
- With reduced broadcast traffic, network congestion will also be alleviated.
- In addition, VLAN can isolate different types of network traffic, such as data traffic and voice traffic, to avoid mutual interference between different types of traffic and further reduce network congestion.
Example:
Suppose there are 20 computers in an office, 10 of which are used for office work and 10 for video conferencing. If one of the office computers sends a broadcast, all 20 computers receive the broadcast, causing network congestion.
Using VLAN, office computers and video conferencing computers can be assigned to different VLANs. In this way, broadcasts sent by office computers will only affect other office computers and not the video conferencing computers, thereby reducing network congestion.
2. Enhance network security
Isolate different departments or workgroups:
- VLAN can isolate devices in different departments or work groups in different logical networks to prevent the leakage of sensitive information and the spread of network attacks.
- Each VLAN can be set with different security policies, such as access control, firewall, etc., to meet the security needs of different departments or work groups.
Improve security:
- By isolating different networks, the risk of broadcast attacks can be effectively reduced.
- In addition, VLANs can restrict communication between different VLANs to prevent unauthorized access.
Example:
Suppose a company has an employee network and a guest network. To prevent guests from accessing internal company resources, VLANs can be used to isolate employee and guest networks. In this way, visitors cannot directly access the company’s internal servers and files.
3. Simplify network management
Independently manage different VLANs:
- VLAN can divide the network into multiple independent logical networks, and each VLAN can be configured and managed independently.
- This makes it easier for network administrators to manage and maintain different network environments, improving network management efficiency.
Improve efficiency:
- Different network policies can be formulated for different VLANs, such as bandwidth allocation, QoS, etc.
- Troubleshooting is also made easier by just focusing on a specific VLAN.
Example:
Consider a corporate network with hundreds of devices, including office computers, servers, printers, etc. Using VLAN, these devices can be divided into different VLANs, such as office VLAN, server VLAN, printer VLAN, etc. In this way, network administrators can develop different network policies for different VLANs and quickly locate and solve network faults.
VLAN application scenarios
As a flexible and practical network technology, VLAN has a wide range of application scenarios, covering many fields such as enterprise networks, data centers, and campus networks. Below we will discuss in detail the specific applications of VLAN in different scenarios:
1. Enterprise network
Divide employee, guest, wireless network, etc. VLANs:
- Dividing different types of devices such as employees, guests, and wireless networks into different VLANs can effectively isolate different networks and prevent the leakage of sensitive information and the spread of network attacks.
- Develop different security policies and access control rules for different VLANs to further improve network security.
Example:
- Separating the employee network into one VLAN and the guest network into another VLAN prevents guests from accessing internal company resources.
- Divide the wireless network into an independent VLAN to enhance the security management of the wireless network.
2. Data Center
Separate VLANs for servers, storage, network devices, etc.:
- Dividing different types of devices such as servers, storage, and network devices into different VLANs can improve network performance and simplify network management.
- Developing different QoS policies for different VLANs can ensure that business-critical applications receive higher priority bandwidth.
Example:
- Group servers into one VLAN and storage devices into another VLAN can reduce interference between different types of traffic and improve network performance.
- Divide network devices into an independent VLAN for easy network management and maintenance.
3. Campus Network
Distinguish between student, teacher, guest, etc. VLANs:
- Dividing different types of users such as students, teachers, and guests into different VLANs can strengthen the management and control of network resources and ensure network security.
- Develop different bandwidth limits and access policies for different VLANs to meet the needs of different users.
Example:
- Divide the student network into one VLAN and the teacher network into another VLAN to prevent students from randomly accessing resources on the teacher network.
- By dividing the guest network into a separate VLAN, you can restrict guest access to the campus network.
4. Other application scenarios
In addition to the above common application scenarios, VLAN is also widely used in hospitals, hotels, government agencies and other fields to divide different network areas to meet different network needs.
FAQs about VLAN
Different switch models vary in the number of VLANs they support, but most switches support hundreds or even thousands of VLANs. Please refer to the equipment specifications for specific quantities.
Devices in different VLANs need to use routers or Layer 3 switches to communicate with each other. 1. The router can route data packets of different VLANs to the target VLAN to achieve communication between different VLANs. 2. In addition to the routing function, the Layer 3 switch can also forward data packets between VLANs to realize communication between different VLAN.
Implementation method: 1. Connect devices in different VLANs to the same router or layer 3 switch. 2. Configure the appropriate routing table or inter-VLAN forwarding rules on the router or Layer 3 switch to forward packets to the destination VLAN.
You can determine whether a device belongs to a certain VLAN in the following ways: 1. View the network interface configuration of the device: The VLAN to which it belongs will be displayed in the network interface configuration of many devices. 2. Use command line tools to query: You can use command line tools to query the VLAN configuration of the device, such as the show vlan command. 3. Use network management tools to view: You can use network management tools to view the VLAN configuration of the device, such as the web interface or SNMP management tool.
VLAN (Virtual Local Area Network) is a logical network segmentation technology. It allows a physical LAN to be divided into multiple logically separate VLANs. VLANs are used to enhance network security, improve network performance, and simplify network administration by grouping devices based on logical requirements rather than physical location.
The main function of VLAN is to divide a single physical network into multiple logical networks to achieve network segmentation. Network segmentation can enhance security, improve performance, simplify management, and allocate dedicated bandwidth to different types of traffic.
A switch is an intelligent hardware device used to connect network devices. It learns and forwards data frames based on MAC addresses. VLAN is a function of the switch that uses the switch’s port division and packet labeling technology to create multiple virtual networks on a single switch.
no. VLAN is a logical concept that uses Ethernet switches to create virtual LANs. VLAN itself is not a physical network type, but a technical means of dividing an existing Ethernet network.